IoT security means preventing threats and breaches from damaging your business by identifying, monitoring, and protecting Internet devices and their connected networks. It means identifying and fixing vulnerabilities from various devices that pose security risks.
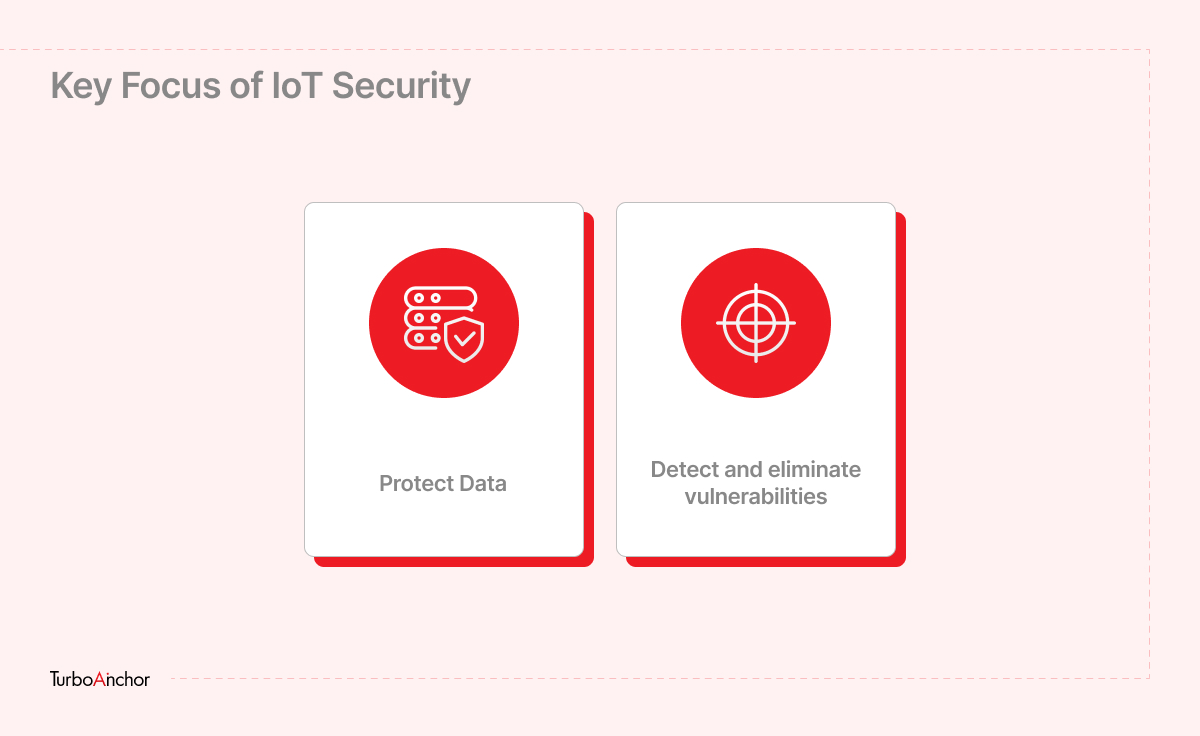
So for sure, anything connected to the Internet is probably to face an attack at one end. In addition to credential theft, attackers can exploit vulnerability exploits to compromise IoT devices remotely. Many IoT devices aren’t built with strong security so IoT security can be quite challenging. Often, manufacturers focus more on features and usage than security in order to get their devices to market fast. While on the other hand the key focus of IoT security are,
- Assure the secure collection, storage, processing, and transfer of all data.
- Identify and remove vulnerabilities in IoT devices.
Suggested Read: All you Need to Know About IoT Solutions
IoT devices are becoming a day-to-day use in our lives for customers and industries that may come across challenges related to IoT security.
What are the Biggest Challenges with Internet of Things Security?
So after getting to know about “What IoT security.” The next thing to know about IoT security challenges tends to face. As discussed earlier, IoT devices were designed by manufacturers focusing more on features and usage than security to get their devices to sell quickly. That ends up leading to likely vulnerabilities in multiple devices. In most cases, it’s not possible to install security software on the device.
Following are the challenges that IoT security faces,
Firmware and Software vulnerabilities
Well, safeguarding the security of IoT systems is a little of a handful because most smart devices are risk-constrained and have limited computing capability. Therefore, they aren’t capable of running powerful tasks and resource-hungry security functions. Most IoT systems face security vulnerability because of a lack of computational capability for robust security measures. Insufficient access control for IoT systems. The small budget allocated to firmware security testing and improvement. IoT devices’ limited budgets and technical limitations prevent regular patches and updates. The users might not update their devices, which restricts vulnerability patches. As with time, older devices won’t be able to receive software updates.
Insecure communication
When it comes to old-school traditional methods, they aren’t that efficient for secure IoT device communication. One of the most notorious threats faced by insecure communications is Man in the middle attack (MITM). If your device does not use authentication and encryption mechanisms, it can easily fall victim to a MITM attack. The device can also be infected with malware or have its functionality altered. But that’s not the end of the story. Even if you don’t fall prey to a MITM attack, the data you exchange with other devices by cybercriminals. Simply, a connected device can end up as a plague. You ask how? If one device gets into an attacker, the other connected devices are also compromised.
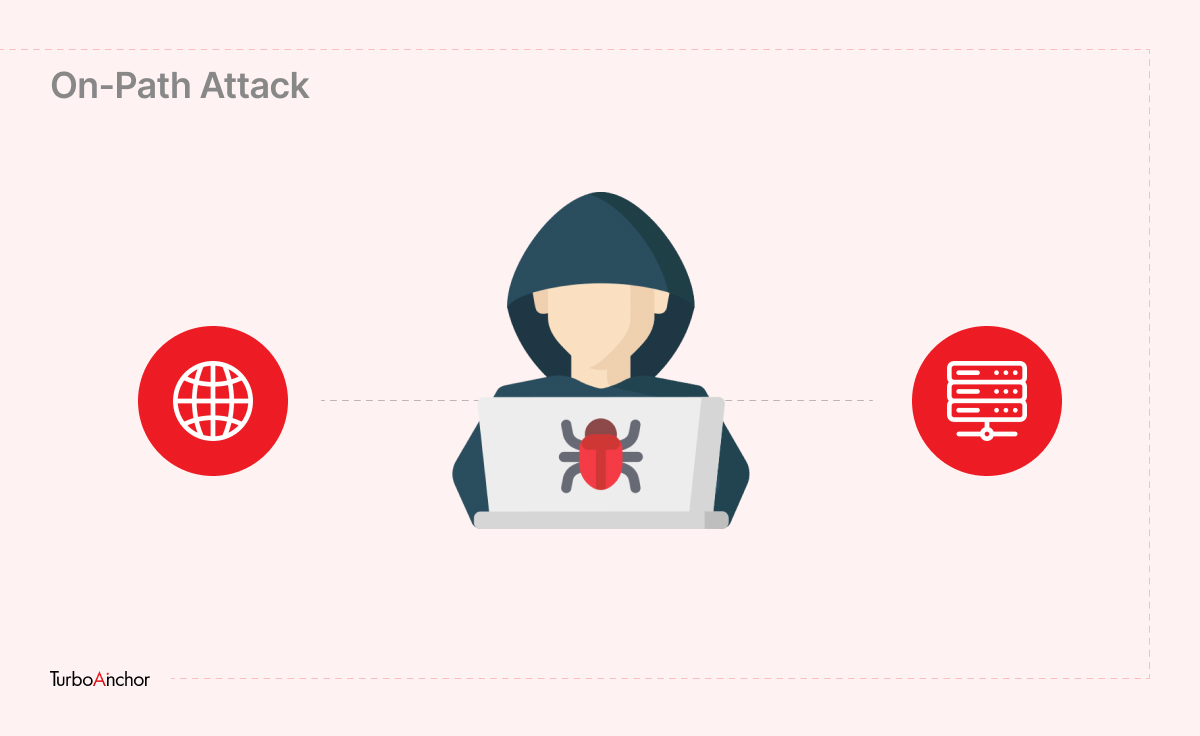
On-path attacks
In on-path attacks, attackers place themselves between parties that trust one another.
For Example, The Amazon-owned company Ring smart doorbells have made quite a name for security incidents in recent years. Earlier for accidentally exposing customer data to Facebook and Google via third-party trackers embedded into their android apps without proper customer consent.
Another Example, an IoT security camera and the camera’s cloud server block communications between them. IoT devices are especially vulnerable to such attacks because many of them do not encrypt (encryption rearranges data so that unauthorized parties cannot understand it) their communications by default.
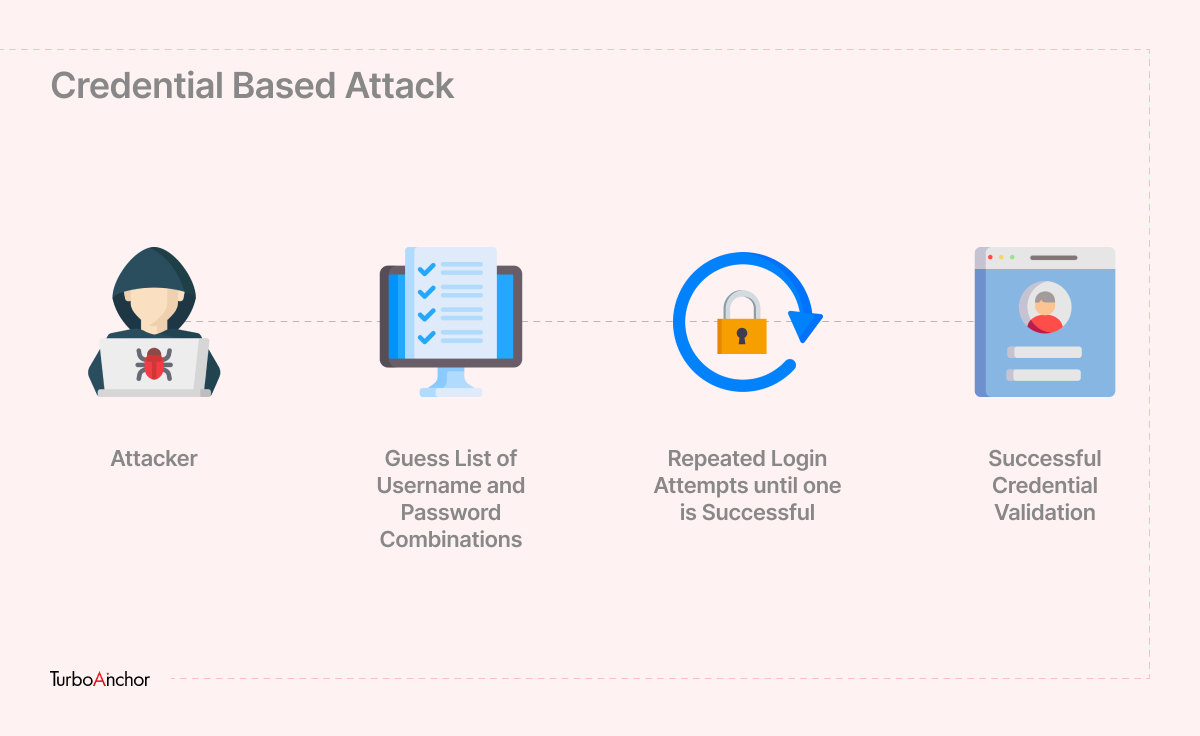
Credential-based attacks
There are several IoT devices that come with default administration usernames and passwords. It is advised to many industries that avoid selling IoT devices that come with poor security credentials. Most usernames or passwords suggested by them are too weak, like Admin as a username or 12*****8 as a password which in some cases can’t be changed or reset. Many successful IoT device attacks happen simply because attackers guess the right credentials. These default usernames and passwords are well known to hackers.
How are IoT devices used in DDoS attacks?
Distributed Denial of service attack is a technique used by hackers to set a Tsunami of internet traffic to a server. That causes users to access that specific site or online service. These attacks are more robust when the attacking party can send them from multiple devices. These attacks are tough to tackle because each device has their own IP addresses that end up being too many.
How do I overcome security issues in IoT?
Well, there isn’t a magic wand that you can spin around and solve your issues, but you can follow these strategies to avoid further risks and threats:
- The first thing you can do is assign someone to act as an administrator of IoT devices.
- You should be aware that vulnerability is one crucial loophole in causing issues for IoT
devices until now. The older the device is, the more the chances of getting infected; therefore, it’s essential to check for patches and stay updated regularly. - Go for strong and unique passwords for all accounts that are hard to figure out for someone trying unauthorized access.
- Enable router firewall, WPA 2 security protocol, and use a strong Wi-Fi password.
- IoT devices can often put your networks at risk. Still, when it comes to networks, they can act as a balancing ground for users to set security measures concerning all devices.
- Go for cloud-based solutions as they can provide security and Secure IoT cloud convergence.
- GPS is just way too much used by some IoT devices as applications that can end up a potential threat on the bases of security. Therefore, any company needs to look after these GPS signals.
Final Thoughts
Lastly, we can say that a business can benefit from IoT applications, but its security is still a major factor. IoT security has been given a lot of consideration nowadays. However, research is being conducted day by day to secure certain industries, monitor IoT related threats and upcoming changes. Regardless of the industry and size, IoT solutions can be made part of any business and help boost customer satisfaction and accuracy.
Suggested Read: